Last Updated: Feb 27, 2022
The transition from Microsoft Active Directory (AD) to Microsoft Azure Active Directory (AAD) has introduced a new concept called Hybrid Domain Join (HDJ). With HDJ a Windows computer first joins AD and then joins AAD allowing the device to consume configurations from both AD and AAD. One of the fastest ways to introduce HDJ into an organization is to enable this through the use of a Microsoft Active Directory Group Policy Object (GPO). This blog walks through the configuration of Microsoft Active Directory to support HDJ.
How to Configure
It only takes three steps to configure support for HDJ in Active Directory:
- Update AD Group Policy Object Definition Files
- Install and Configure Azure AD Connect
- Enable Device Registration in AD GPO
Step 1: Update AD Group Policy Object Definition Files
There are some whacky things about AD that seem to defy conventional logic. One example of this is Group Policy Object (GPO) management. With each new release of the Windows Operating System a new set of configuration options are available on the device that AD GPO needs to be made aware exist. When Windows devices are joined to a domain, the primary configuration method for the device is going to be the AD GPO’s. One would think the GPOs would get updated with the new configuration options automatically by Windows Update, but they do not. Instead, IT Administrators must follow an overly complex process to update what Microsoft calls the Policy Definition Files.
Microsoft creates hundreds of definition files for each major build of Windows and each one is stored in file type of *.ADMX. These *.ADMX files are bundled into a *.MSI available for download from Microsoft’s website. The advantage of this methodology is that IT Admins can choose to update All or only some of the *.ADMX files based on their specific configuration requirements. For Hybrid Domain Join to function, the AD Domain Controller needs to be running the Windows 10 1803 or newer Policy Definition Files. Here’s what you need to do to update these:
- Each major build of Windows receives a new Policy Definition Files which means this process will need to be repeated each time Microsoft releases a new major build of Windows. The good news is that they are backward compatible so if you’ve skipped a few you only need the latest one. Here are a couple of links to Microsoft’s website to download the latest versions as of this blog post:
Download Windows 10 November 2021 ADMX files from Microsoft.com
Download Windows 11 October 2021 ADMX files from Microsoft.com - The MSI downloaded does not install the templates, it just extracts them to a subfolder with the name that matches the version you downloaded. For example:
C:\Program Files (x86)\Microsoft Group Policy\Windows 10 October 2020 Update (20H2)\PolicyDefinitions.
With the files extracted move the files to SYSVOL as described in the next step. - With the files now extracted, use Windows File Explorer to copy the contents of the PolicyDefinitions folder from
C:\Program Files (x86)\Microsoft Group Policy\Windows 10 October 2020 Update (20H2)\PolicyDefinitions
toSYSVOL\YOURdomain\Policies\PolicyDefinitions\folder on your DC.
In my lab, my domain is named lab.aftersixcomputers.com so my SYSVOL folder that I need to copy these to is\\lab.aftersixcomputers.com\SYSVOL\lab.aftersixcomputers.com\Policies\PolicyDefinitions. Adjust the folder path for your domain name.
The end result will look like this: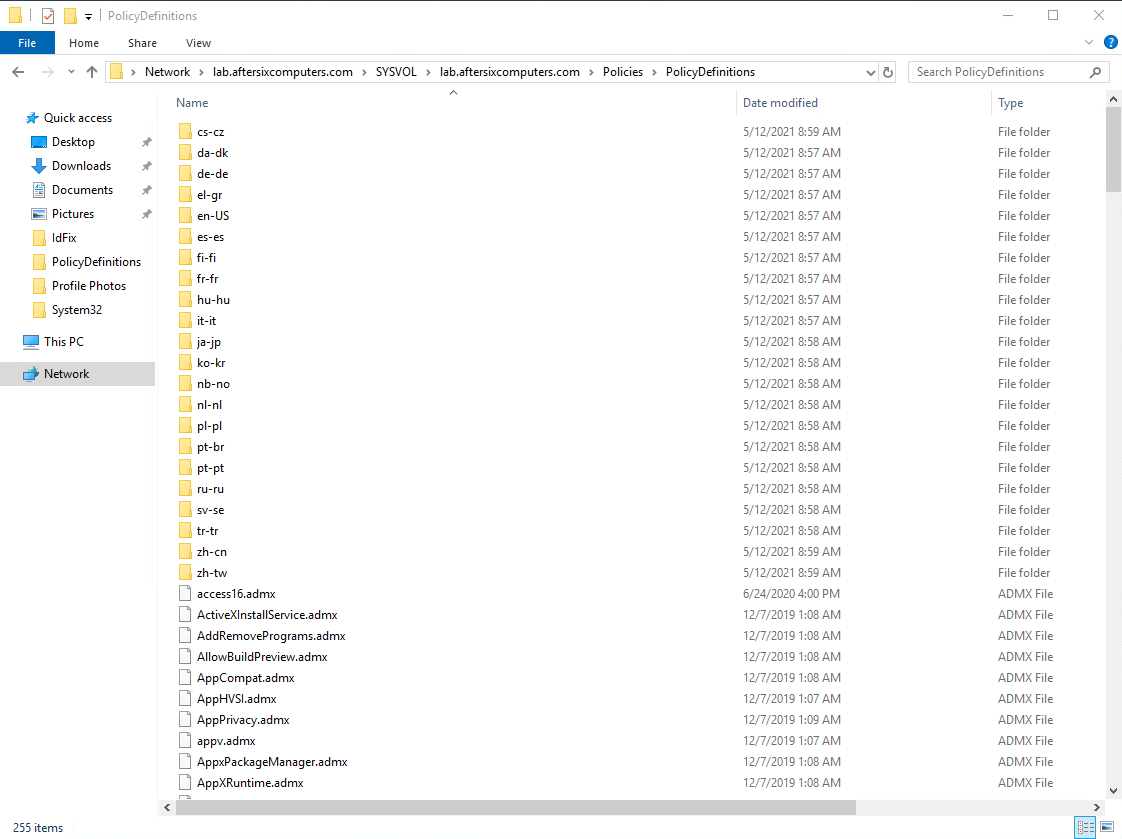
It’s worth noting that in versions of the MSI targeted at earlier releases of Windows 10, the extracted directory incorrectly added a space between the folder Policy and Definitions, making the folder that gets extracted end up with the name Policy Definitions instead of the required PolicyDefinitions. Make sure your PolicyDefinitions folder does not include a space. While this behavior appears to be corrected in the 20H2 release of the MSI, watch out for this if you are downloading older versions. - Depending on your Domain Infrastructure, you’ll need to wait for AD replication to occur so that these new files are replicated across the entire domain. Once AD replication completes you’ve now successfully updated the GPOs to support all the new Windows features, which in our case includes Hybrid Domain Join.
Step 2: Install and configure Azure AD Connect
Microsoft Azure AD Connect is a one-way sync tool of user accounts and other configuration items from AD to Azure AD. What you may not realize about the tool is that Microsoft updates it on a regular basis as they continue to change Azure. The tool does not include any auto-update functionality so you’ll have to download a new .MSI and run through an installation, then a set of configuration tasks to upgrade the existing installation. At the time of this writing 1.6.4.0 was the latest version. If you don’t know which version you have installed from the Windows Server running the tool, open the Start Menu > Settings > Apps and Features and you’ll see the version information under the program entry.
Here’s a link to Microsoft’s Download page for the tool:
https://www.microsoft.com/en-us/download/details.aspx?id=47594
Post install and upgrade, you’ll need to make sure you have the Device Options configured to allow Hybrid Domain Join to function. Launch the tool, choose Configure Device Options and walk through the next several configuration screens shown below to enable Hybrid Domain Join functionality.
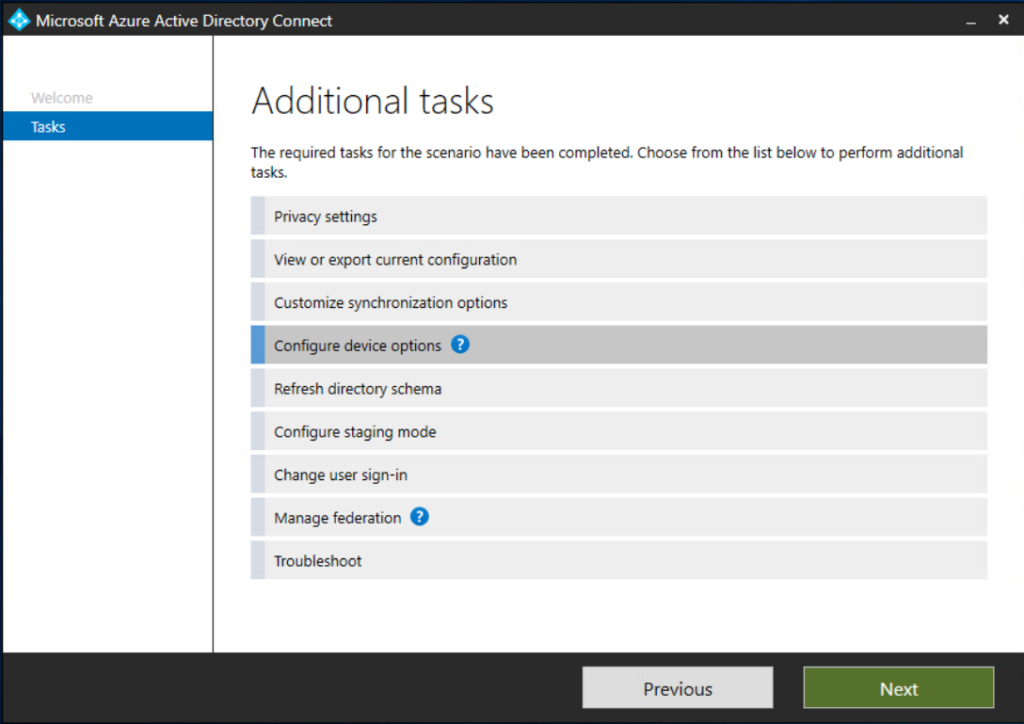
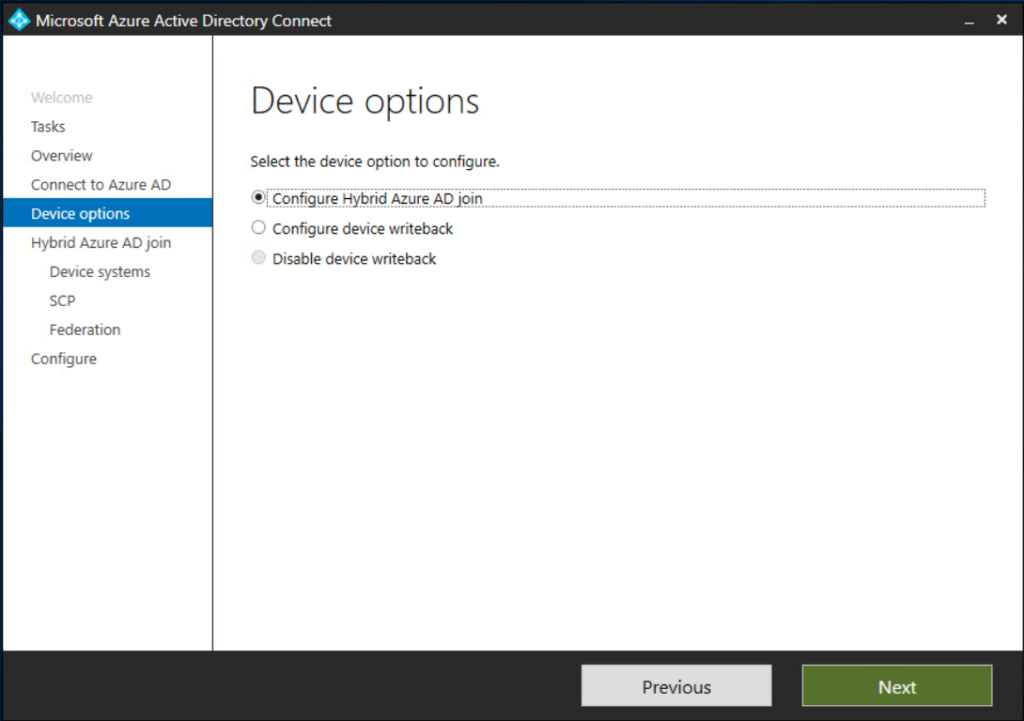
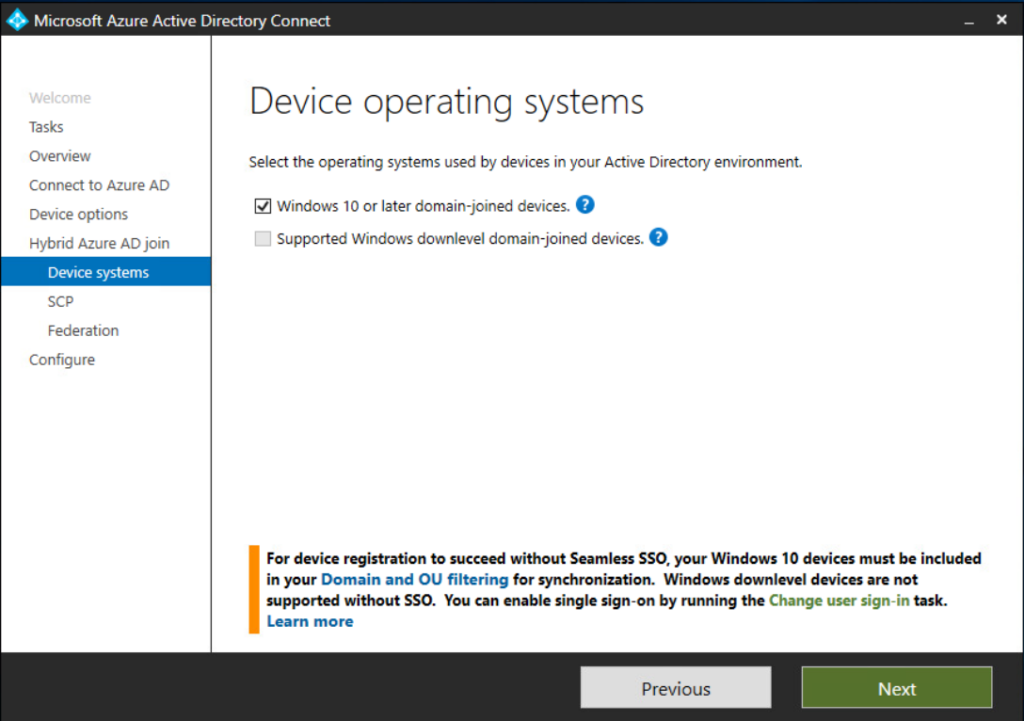
The next two steps of the wizard require SCP and Federation configuration, a topic I won’t go into detail on here. BUT YOU MUST ENABLE SCP or the Hybrid domain join process will fail.
Microsoft provides additional documentation on SCP here:
With Azure AD Connect now configured to support Hybrid Domain Join, the next step is to configure the AD GPO for Device Registration.
Step 3: Enable Device Registration in AD GPO
The final step is to configure a new GPO object to enable the Device Registration. Once this is enabled, any Windows 10 device that joins AD will trigger AD Connect to generate a computer object in Azure for the device.
- Open Group Policy Management Editor
- Right-click on your Domain and choose “Create a GPO in this domain, and Link it here…”
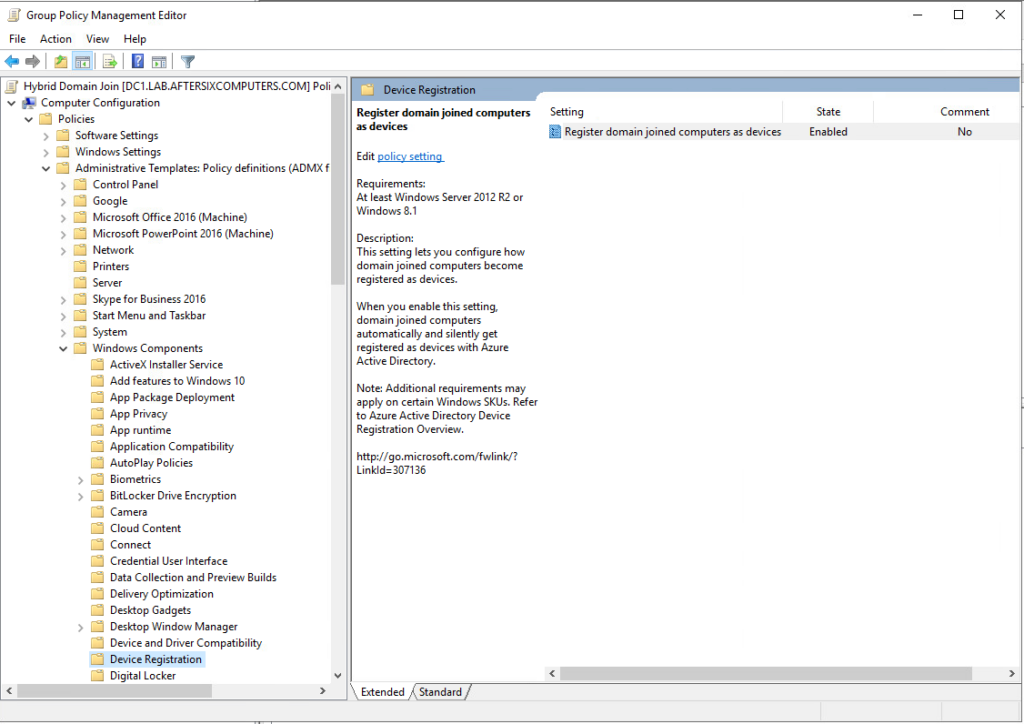
- Navigate to Computer Configuration > Policies > Administrative Templates > Windows Components > Device Registration as seen below.
- Enable the setting “Register domain joined computers as devices” as illustrated below
- With this in place, Microsoft recommends a few other things to think about as documented here: https://docs.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-fed-hybrid-azure-ad-join-post-config-tasks
In Summary
With the previous steps completed, any computer that joins the Domain will now have a corresponding Azure AD computer account record created. Keep in mind that in this model end users will still authenticate to Windows using the AD account, not an Azure account.
Additional Documentation from Microsoft
There are all types of ways to complicate this above configuration so a few links from Microsoft are included below which cover some of these more complex setups:
https://docs.microsoft.com/en-us/azure/active-directory/devices/hybrid-azuread-join-control
https://docs.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-device-writeback
https://docs.microsoft.com/en-us/azure/active-directory/devices/hybrid-azuread-join-control
