Last Updated 5/9/2021
In short, this is a big one for Dell shops. Thank you Maurice Daly! who published a great write up on this issue which you can view by clicking here including links to Dell’s page and Sentinel One’s site.
If you’re using Workspace ONE UEM, below I’ve used Maurice’s scripts as the foundation for resolving this using Workspace ONE UEM Sensors + Apps & Books + Intelligence. Here’s how I did it:
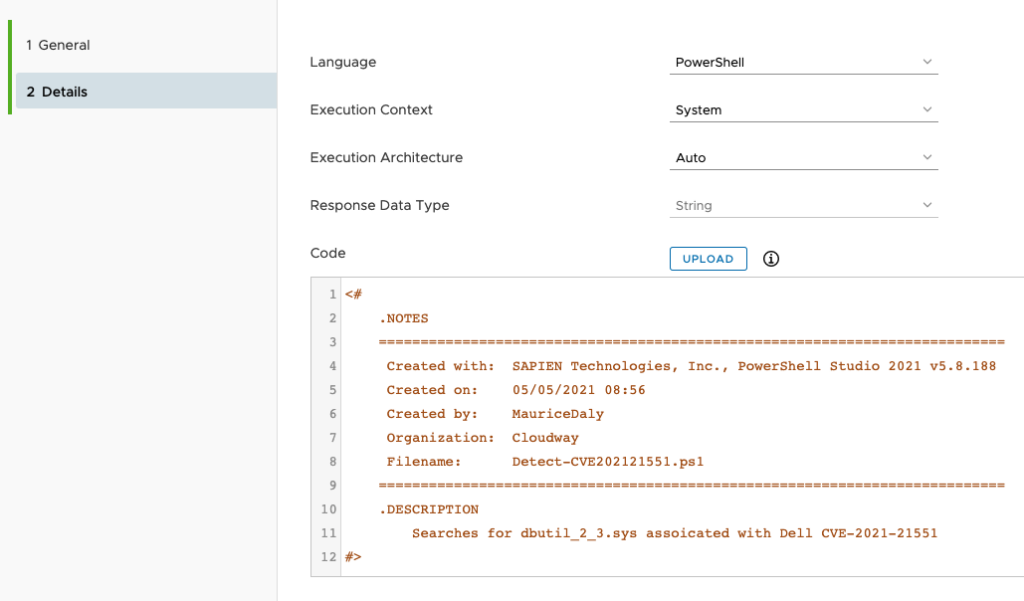
Start by creating a new Workspace ONE UEM Sensor using the Detection script Maurice wrote:

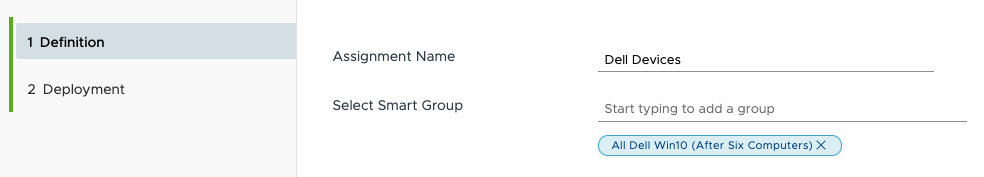
Assign the script to run against all of your Dell Systems:
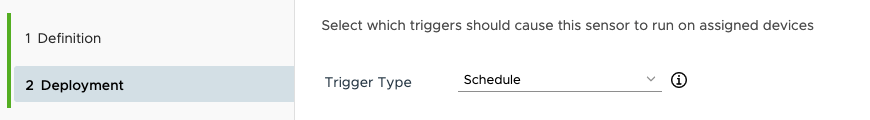
Assign the script to run on a schedule because there are all kinds of ways for this thing to get re-introduced into your environment over the next couple of weeks.
Next create a .ps1 and a dummy.exe then zip them and upload them to the Apps & Books in Workspace ONE UEM. I’ve done this for you if you want just download it here:
Below is the way I setup the Apps & Books:
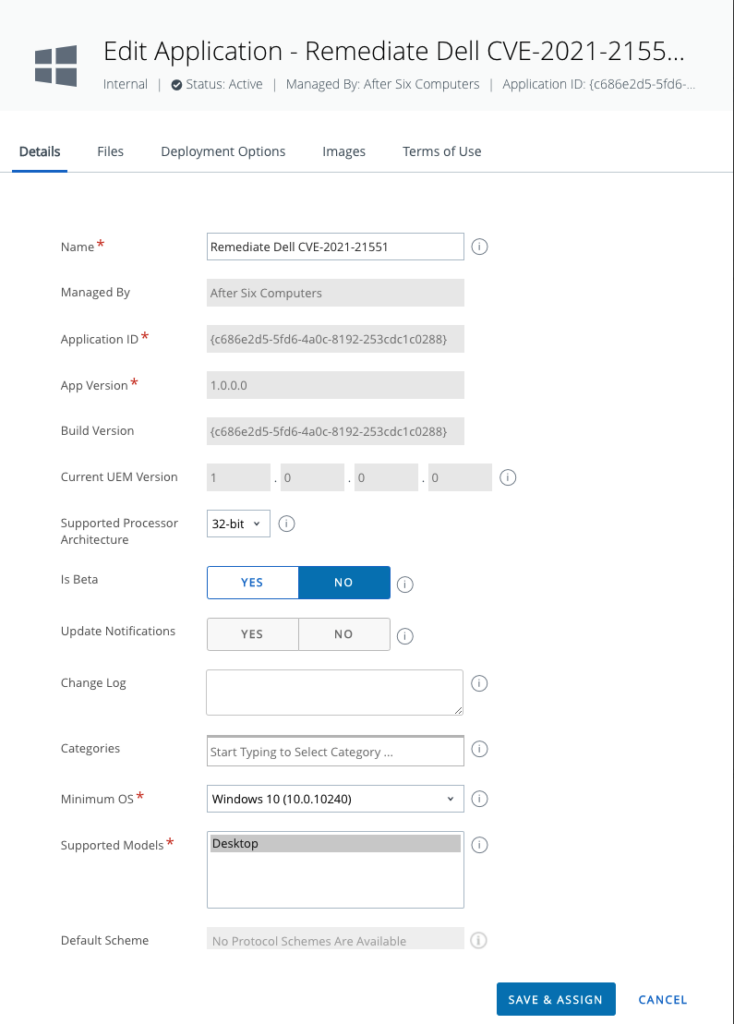
Note that you must provide some type of uninstall and in this case I’m just using N/A:
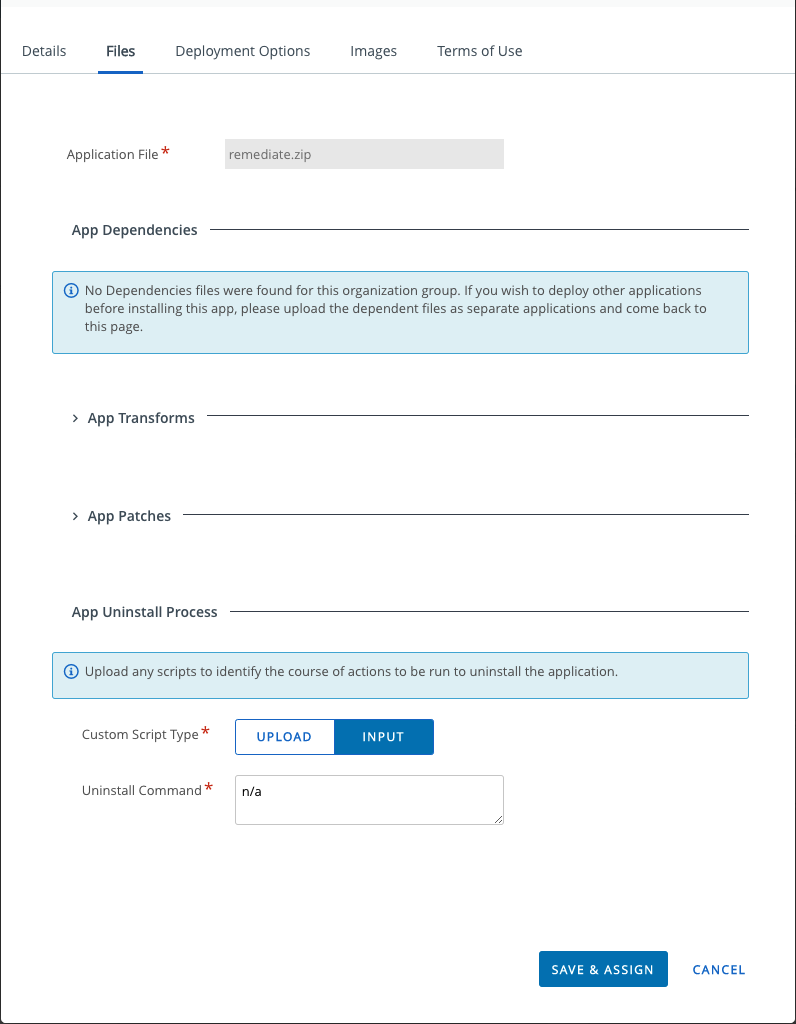
Under Deployment Options the Install Command gets cut off in the screenshot, but the complete command is as follows:
powershell -executionpolicy bypass -file .\remediate.ps1
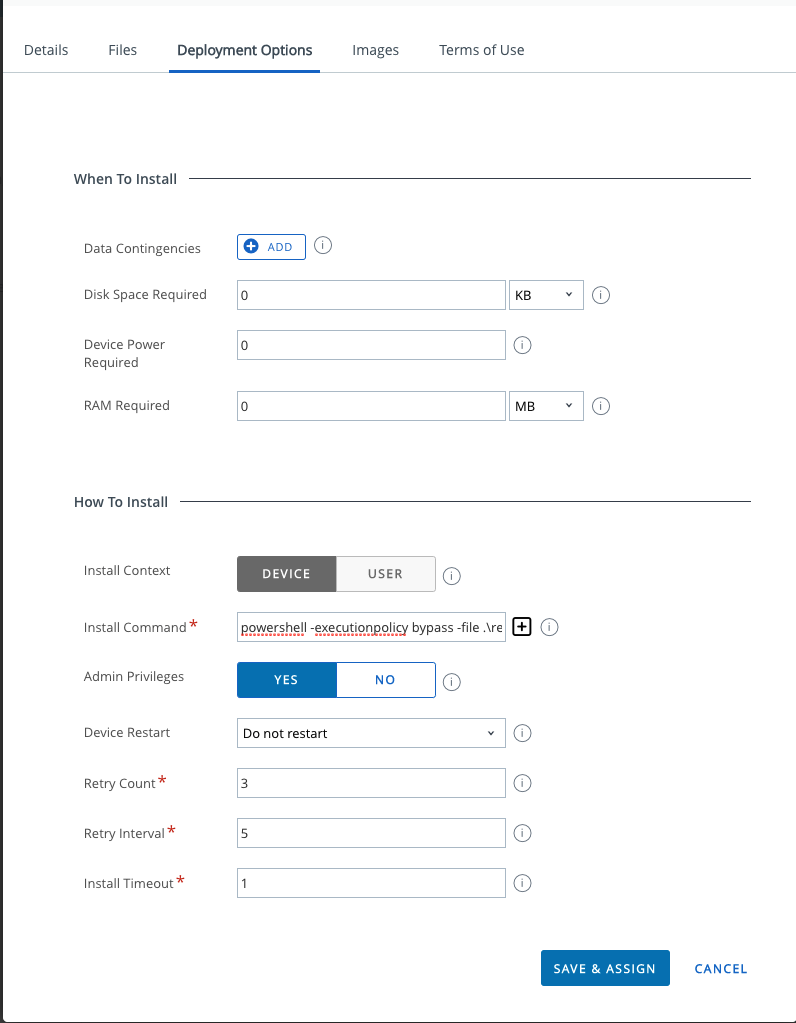
Scrolling down to the “When to Call Install Complete” section, I’m using “File Does Not Exist” and pointing to C:\Windows\Temp\dbutil_2_3.sys”
For Assignment and Distribution, I’m going with the assumption that every Dell device is currently vulnerable so I’m targeting All Dell Devices and running this with App Delivery Method Auto.
Reporting with Workspace ONE Intelligence
I suggest running the Sensor on a test system, and then let at last 30 minutes pass for the Sensor results to be forwarded to Workspace ONE Intelligence before continuing.
My original goal was to use a report in Intelligence as the source for devices still vulnerable. From the report results in Workspace ONE Intelligence, clicking the Automate button would then fire off the App that remediates this. It sounded good in theory but at the time of this writing Workspace ONE Intelligence does not support join operations between Sensors and Reports which means the Automate button is greyed out. I hope that future versions of Workspace One Intelligence will solve this gap. In the meantime the report is still useful to have for reporting:
First build a report using the Sensor and the Sensor results as follows:
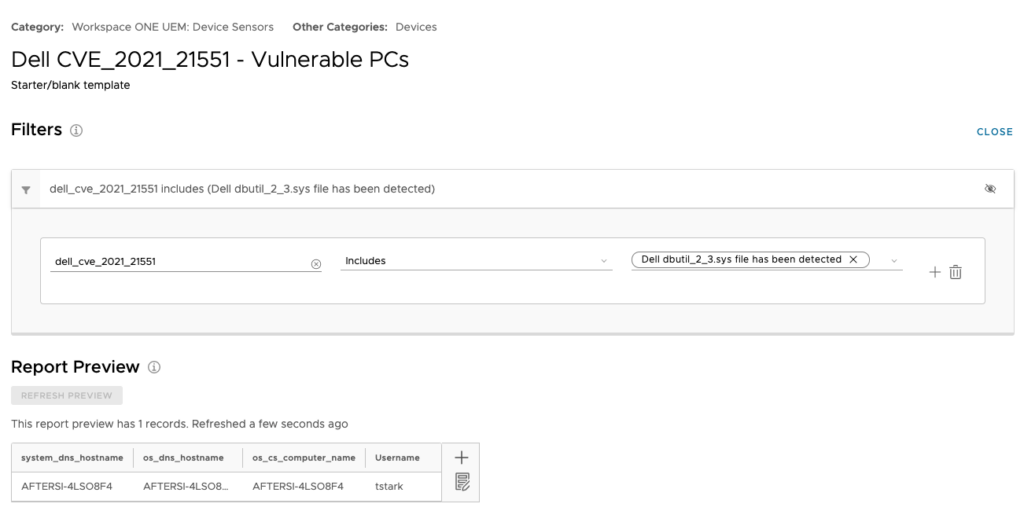
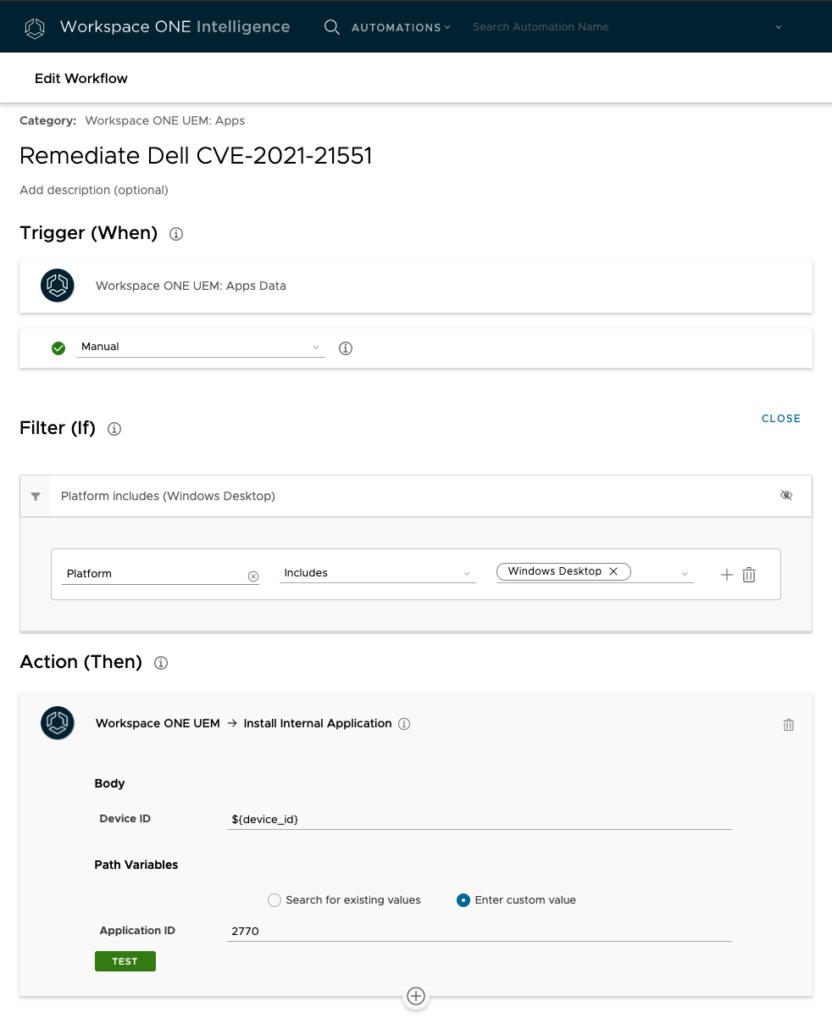
Below is the Automation Rule I was going to trigger. Of note below is that the Application ID will be unique to your environment. To find this value, in the Workspace ONE UEM console, open the Apps & Books section, navigate to the App and click on the link to expand the app details. In the web brower’s address bar, look for the ID for the application then use it for your automation.
Given the inability to run this automation on demand, you might want to change this to run on a schedule.
And that’s it. While this is only one of many possible ways to solve for this, I hope it helps.
P.S. Rumor has it that Dell plans to address this specific vulnerability on Monday May 10th through the Dell Command Update tool. While I hope that happens, there are always plenty of other vulnerabilities across the rest of the IT Software industry, so techniques like the one above will continue to come in handy.